By Lisa Rein
After the January 11th event, I have to admit, nothing has been quite the same for me.
We learned not only about Aaron and the FBI Al Qaeda phishing expedition that left Aaron with an “International Terrorism Investigation” code in his FBI database file forever, but we also learned about all of the critical information that Property of the People is unearthing with its FOIA lawsuits.
Index of topics:
2-Mapping out patterns of FBI FOIA non-compliance
3-Documents POTP acquired from Aaron Swartz’ file
4-Understanding the Metadata Codes within FBI documents
5-Documents POTP sued for and got access to regarding Nelson Mandela
1-Introduction
On January 11, 2019, we had our first Raw Thought Salon at the DNA Lounge in San Francisco. (The next on is on March 8, 2019. TICKETS.) The event was hosted by Lisa Rein (Co-founder of Creative Commons, Aaron Swartz Day, and The Aaron Swartz Day Police Surveillance Project) and Ryan Shapiro, from Property of The People, was the special guest that night.

Ryan is widely known as a leading expert on the Freedom of Information Act and is Executive Director of the transparency non-profit Property of the People. Politico describes Ryan as “a FOIA guru.” MuckRock describes Ryan as “a FOIA superhero.” The FBI argued in federal court that Ryan’s MIT dissertation FOIA research methodologies are themselves a threat to national security.
Ryan is an historian of national security, the policing of dissent, and government transparency. In addition to being a longtime activist, Ryan holds a Ph.D. from the Department of Science, Technology, and Society (HASTS) at the Massachusetts Institute of Technology and is a former Research Affiliate at the Berkman Klein Center for Internet & Society at Harvard University.
We had almost 50 people there. There was a lot discussed, and we learned a ton about FOIA requests and FOIA lawsuits, using Property of the People’s lawsuit as an example (which requested information about Aaron Swartz’ FBI & DOJ files).
It was really fun and informative and many people came up to me afterwards and said what a great time they had – and that they had learned so much. For this reason, we are having one this Friday, March 8th. (Although this time, we’re hoping for a little help with our event costs.)
Ryan explained a few important concepts that we needed to learn first, before we could really dig in to the documents he (at Property of the People) recently uncovered from Aaron’s FBI file.
2-Mapping out patterns of FBI FOIA non-compliance
This post is Part Two of our Full Coverage of the January 11 Raw Thought Salon with Ryan Shapiro. Full Index here.
Ryan began by explaining his methods for mapping out patterns of FBI FOIA non-compliance.
“While doing this,” he explained, “though not as useful as a positive result, a negative result can still often be informative. Each FBI response to a FOIA request functions as a submarine ping as we try to map the ocean’s floor.”
He began to learn the ropes and realized that the FBI has numerous techniques to avoid complying with FOIA while pretending to be in compliance. Techniques that block the release of information.
First, Ryan gave us some important background history:
Ryan: FOIA was only expanded in 1974 to apply to the intelligence agencies, and it’s the first time in the history of the republic that federal intelligence agencies have any sort of real public oversight. And the FBI and other agencies have done everything they can to exempt themselves from it. Since then, the FBI, in some ways more than any other agency, will do nearly everything within its power to avoid compliance with FOIA.
The true purpose of the FBI’s FOIA section is to maintain the FBI’s functional immunity from the Freedom of Information Act. That’s its function.
The Freedom of Information Act doesn’t require an agency to locate the requested records. It requires an agency to conduct a search of reasonable calculated to locate the requested records. This means FOIA requires agency do a good job looking for documents, not that they find anything.
Exploiting this provision of FOIA, the FBI has designed a series of “Failure by Design” FOIA search protocols. The FBI conducts its FOIA searches in such a way that the vast majority of those searches fail to locate the requested records, even though the FBI absolutely has those records. So, the FBI superficially appears to be in compliance with FOIA because it conducted a search, but it doesn’t have to release any documents because that search (deliberately) found nothing.
So, when the FBI writes a FOIA requester claiming there are no records, the letter probably actually said something like, “We have conducted a search of our Central Records System and were unable to identify main file records responsive to your request.” It’s important to remember that this does not mean they don’t have the documents. It means they looked for the documents and didn’t find them. And what it very probably also means is that they looked for the documents in such a way that they almost certainly wouldn’t be found.
Once I figured out how to circumvent many of the FBI’s dirty tricks for FOIA non-compliance, we started getting documents. A few thousand. Then the FBI was like, “Ha ha. Fuck you. You can do that, but watch what we can do.” And then, they just sat on their hands and did nothing.”
The Freedom of Information Act is one of the most under-appreciated elements of the entire American experiment. The notion that the records of the government are the property of the people, and all we need to do to get them is to ask for them, is radically democratic. But FOIA is broken. And one of the main reasons it’s broken is that it has no teeth. There are no penalties for non-compliance. However, FOIA has a little baby tooth, which is, you can sue.
So I sued. After teaming up with attorney Jeffrey Light. He and I now run Property of the People – check it out at propertyofthepeople.org – it’s the transparency organization that we run and that’s how we got the documents from Aaron’s file.
When we first sued, the FBI turned around and said, “Yeah, we’re not going to comply even in court because your MIT dissertation FOIA research experimental methodologies are themselves a threat to national security and so much so that we can’t tell you why – and the FBI asserted this in the form of an ex parte in camera declaration – a secret affidavit from the counter terrorism division of the FBI to the judge about why they can’t tell us why my FOIA methodologies are ostensibly such a threat to national security. (End of Ryan’s quote.)
3-Documents POTP acquired from Aaron Swartz’ file
This post is Part Three of our Full Coverage of the January 11 Raw Thought Salon with Ryan Shapiro. Full Index here.
Lisa Rein: Ryan, could you please talk specifically about what you had to do to get those records about Aaron. And then please explain to us what they even mean; those two little pages that you found. (#1, #2) (That had never been shown to the public before.)
Ryan: Sure. One of the things that we did is to go after FBI records on Aaron Swartz. We wanted to understand the FBI’s role in going after Aaron. We knew that other folks were filing FOIA requests and had cases going – Kevin Poulsen for instance, (swartzfiles.com) – and we wanted to complement those efforts.
So we submitted a FOIA request to the FBI for records on Aaron. As per their usual, the FBI refused to comply, so we sued. We got some documents, as did Kevin Poulsen, but we knew the FBI had more.
First of all, that the FBI only had PACER-related records on Aaron seemed totally implausible. I mean, we still have no JSTOR records.
We analyzed the documents we and others received, including the FBI metadata in those documents. We saw there was a reference to “315T” document involving Aaron. 315T is FBI code for an International Terrorism Investigation. And we were like, “Hey, what the fuck is this? Where is this document? The International Terrorism Investigation one? We want it. Why don’t we have it?” And the FBI was like, “Oh, right, yeah. Your request was for documents about Aaron, and that document isn’t about Aaron. It’s about Aaron’s website and email address, not Aaron. So it’s not responsive to your request, so you can’t have it.” And we were like, “What the fuck? No. We asked for any and all documents relating or referring to Aaron. If it’s about Aaron’s website (it says aaronsw.com) (see below) and email, it’s definitely about Aaron and definitely responsive to our request.”
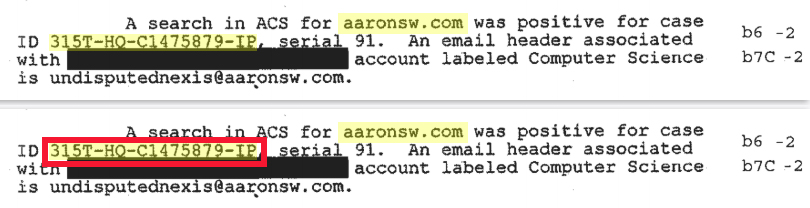
And the FBI went so far to say – and again this behavior is not special for this situation with Aaron. This pertains to the FBI’s absolute anti-FOIA position. The FBI said that records pertaining to Aaron’s domain and his email are not about him. And we’ve been literally fighting about this point for years, in Federal Court. And recently won on that particular point.
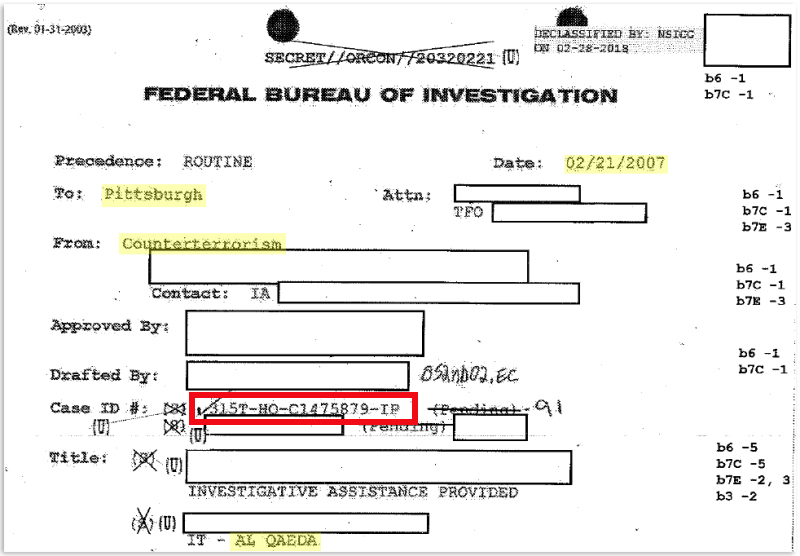
That’s how we got these documents (#1, #2) . We only got two pages out of we don’t know how many, but it’s definitely dozens of pages in this document, and it’s a “315T” so an FBI “International Terrorism Investigation” pertaining to Al Qaeda investigation.
So, Aaron got pointlessly swept up in some FBI Al Qaeda investigation. And then, when the FBI was doing its PACER investigation, and they’re like, “Alright, let’s see what we’ve got on this kid.” And then this record comes up, and they’re like, “Oh, look at this: Al Qaeda; International Terrorism.”
Lisa: So let me get this straight. If the FBI is looking up Aaron in its database, his record comes up with a reference to this “315T” document, right?
Ryan: Exactly. And that’s how we even became aware of the document to being with. It was in the FBI’s PACER file on Aaron.
And what these two pages of the document show is that FBI Headquarters in 2007 was doing a 315T International Terrorism Investigation of Al Qaeda. We don’t know specifically about what. It’s not Al Qaeda in general. It’s some specific thing pertaining to Al Qaeda that had some sort of nexus with the University of Pittsburg.
And FBI Headquarters tasked the Pittsburgh field office of the FBI with figuring something out. And we don’t know what. But the Pittsburg Field Office of the FBI said, “Ok, but we need you to get from the University of Pittsburg a whole bunch of metadata – mail headers and that sort of thing – associated with the University’s Computer Science Department and Computer Services and Systems Development office (CSSD). FBI Headquarters got this metadata from the University for the FBI’s Pittsburgh field office. These two pages we have from the 315T investigation are part of FBI Headquarters getting back to Pittsburg with that metadata.
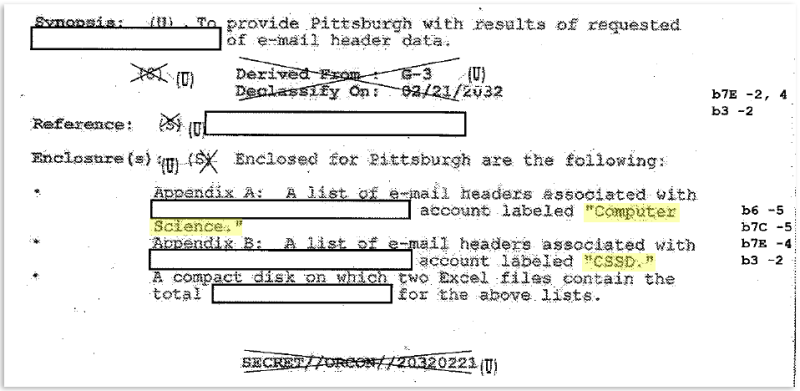
So, the documents we obtained (#1, #2) show FBI Headquarters getting back to Pittsburg saying, “Here’s the information you needed, a whole bunch of email header data from the U. of Pittsburgh Computer Science Department and CSSD. One important question here is though, “How did the FBI get this data? Because they likely did not get a warrant for it.”
According to Dell Cameron’s excellent article in Gizmodo on the documents we obtained, which I strongly encourage everyone to read, because it’s excellent and goes into far greater detail, it’s likely the FBI used a National Security Letter or Letters to obtain the information, which the Bureau was able to do at that time with little restraint.
If Dell’s article is correct on this point, these National Security Letters were used to scoop up who knows how many people’s data. We know it’s dozens of pages (at minimum – we don’t know the maximum) of people’s metadata. Who’s metadata? Anyone who had some sort of association with the Computer Science Department or this other related entity (CSSD) at the University of Pittsburg at a particular point? Who knows? The FBI has withheld this information from us on “national security” grounds.
And all this information is stored indefinitely in FBI databases, associated with International Terrorism, for who knows what reason. Maybe these folks were on a university mailing list. And then, literally years later, when Aaron is being investigated in – I mean it was a bullshit investigation anyway – for PACER. For uploading public court records, court documents, to the open web. The FBI was then able to be like “oh look International Terrorism. Al Qaeda.” It’s unclear if it influenced the FBI or the DOJ’s egregiously fucked up prosecution of Aaron in the JSTOR case. There’s no specific information at present to suggest that it did, but the possibility certainly exists.
Remember though, the FBI DOJ don’t need a special reason (like being coincidentally linked to an Al Qaeda investigation) to destroy people’s lives. The culture of the FBI, what’s driving most of the case agents, is a sales culture. It’s Glen Garry Glen Ross. They’re sales people as much as they’re investigators, and closing cases that result in convictions is their version of sales. Because agents who produce convictions get assigned better cases the next time. It doesn’t matter if the conviction they ultimately secure is even related to the crime, or the even the person originally targeted in the investigation.
The FBI is of course an investigative agency, but “investigation” as most people think about it isn’t really how the Bureau produces most of the evidence the DOJ ultimately uses to secure convictions. In so many cases, the FBI operates primarily by bullying people into providing evidence against themselves or others that the FBI otherwise would not have gotten. This is also a lot of what the DOJ does too.
At the agent level and at the prosecutorial level, it has to do with the score card. It’s just the number of wins, because then you get better gigs the next time. You get better cases as an agent, promoted as a Prosecutor. — end Ryan quote.
Lisa: Ah, ok. Just like with Stephen Heymann and Carmen Ortiz, who were trying to build up their careers by making an example out of Aaron.
Ryan: Yes. It’s just straight up career advancement.
4-Understanding the Metadata Codes within FBI documents
This post is Part Four of our Full Coverage of the January 11 Raw Thought Salon with Ryan Shapiro. Full Index here.
Lisa: Ryan, please explain to us what you meant when you explained to me that you were effectively able to make meaning out of the FBI metadata codes. In the case of the pages from Aaron’s FBI that you obtained (#1, #2), when I look at the exact pages that you got back, they didn’t look like anything to me because so much of them had been redacted. But you helped me understand how the most useful information on them was in the metadata codes they used.
Could you explain a bit more about those metatdata codes? And how you even got to that point?
Ryan: Sure. In this particular case, everything we had gotten before helped get us there. It was an iterative process. In this particular case, we identified the FBI Case ID 315T-HQ-C1475879-IP on one of the released documents, and subsequently we’ve spent years fighting about it in court. In part it was out intimate familiarity with FBI records systems that allowed us to prevail.
Lisa: But I mean, was it a mistake when they gave you the first document with the case number on it?
Ryan: No. It wasn’t so much a screw up really. It was more just that most people don’t know what the codes means, so they don’t know what they’re looking at when they see them.
Lisa: Where do you get the list of these codes and things that your talking about. You had to reverse engineer it, right? Are you keeping a list yourself?
Ryan: There are some publicly available partial lists, but there isn’t a publicly available full list, although we are currently suing for one. And a lot of the codes are still classified or otherwise kept secret by the FBI. We’ve obsessed over this issue for years, filing numerous FOIA requests and lawsuits for information on the codes, doing archival research for information on the codes, going through agency declarations in other folks’ past and ongoing FOIA lawsuits, etc.
Knowing these codes can often help in circumventing the FBI’s bullshit FOIA search protocols, as well as of course help in deciphering FBI documents.
We recently determined the FBI’s file classification code for the Black Lives Matter movement, which the FBI perversely refers to as “Black Identity Extremists” – the Bureau’s new bureaucratic umbrella for targeting as terrorists black people who expose the daily terror against their families and neighborhoods perpetrated by unaccountable killers in blue.” Using the FBI’s file classification code for Black Identity Extremists, we now have a lawsuit going after the these records. This lawsuit complements our other BLM/BIE lawsuit against the FBI and a number of other agencies, as well the related FOIA work being done by other groups such as Color of Change.
Question from an audience member: Do we have tips regarding narrowing down our FOIA requests or how to respond when one gets a denial.
Lisa: Well there’s the Aaron Swartz Day Police Surveillance Project – which provides letter templates and strategies for doing just that.
Ryan: It really depends on the agency. Because FOIA has no penalties for noncompliance, and an agency that doesn’t’ want to comply has very little incentive to do so. And as we’ve already discussed, the FBI will do nearly everything within its power to maintain its functional immunity from the Freedom of Information Act.
But some agencies, both at the federal and local level, are not nearly as venomously hostile to FOIA as the FBI. There’s FOIA, the federal Freedom of Information Act, and then each of the 50 states also has its own state level open records laws. The Aaron Swartz Day Police Surveillance Project is an excellent example of how FOIA and other opens records laws can work when targeted at agencies which are not inherently hostile to open government.
Lisa: Yes, for the most part, these local law enforcement agencies are totally complying. We aren’t experiencing the kind of behavior that Ryan explained earlier re: the FBI’s systematic denial as a matter of policy.
Ryan: The ASD PSP does amazing open records work with agencies all over California. Another example of a group doing stellar work along similar lines is Lucy Parsons Labs, which is doing is doing powerful open records work in Chicago, California., and federally (Hear Freddy Martinez speak at Aaron Swartz Day 2018 here.) this includes LPL’s going after surveillance records, as well as records on Berkeley PD’s doxxing of Antifa activists.
Question from an audience member: To what extent has your worked involved taking information that you found in one FOIA request; terminology, phrasing, references – and being able to take that and use in future FOIA requests, to get more information. How do you keep refining it down to the point where they have to give you something?
Ryan: Our work is deeply iterative, in that we’re routinely mining documents we’ve gotten through FOIA requests and litigation for information to serve as the basis for subsequent FOIA requests and litigation which in turn produce additional documents which themselves serve as the basis for yet another round of FOIA requests and litigation, and so on.
But in terms of taking phrasing from one FOIA request for use in subsequent FOIA requests, it really depends. Again, it depends on which agency you’re dealing with. With agencies overtly hostile to FOIA like the FBI, to a certain extent, it doesn’t entirely matter what language you use unless you plan to sue. The FBI doesn’t really care what language you use. Most of the time, they’re very likely to deny or otherwise avoid compliance with your request no matter how you write it.
But if you are going to litigate, then it’s a different story, and how you write the request matters a great deal. It’s important to note that in these cases, you’re not really writing the requests so much for the agencies as you are for the judge who you hope will force the agency to comply with the law (FOIA). So, when you go before a judge, you can say “This is how we crafted the request. Here’s the case law on that. This is how the FBI responded. Here’s the case law on that…” For what it’s worth, in addition to trying to get the documents we’re after, one of the things we try to do at Property of the People is to break and rebuild FOIA case law so that FOIA can in fact be a tool everyone can use successfully.
For example, sometimes these otherwise obtuse agencies try to get all philosophical on us in order to avoid compliance with a FOIA request in litigation. So, requestors will generally ask for “any and all records relating to Subject X.” But CIA for years has refused to process such requests by getting all existential and disingenuously arguing in court that they don’t know what “relating to Subject X” means because “what does it really mean for something to relate to something else? Everything relates to everything else in one way or another, so the requestor could be asking for anything, and therefore your request is overbroad.” And sure, in a sense everything relates to everything else. Of course the CIA knows what “any and all records relating to Subject X” means. But the CIA succeeded in establishing case law beneficial to them, so if one requests records “relating to” Subject X, CIA can say “fuck you” and deny your request on those grounds.
In part for this reason, we set up a FOIA lawsuit that ultimately allowed us to beat the CIA in court and create new case law on this question that allows requestors to use language that at least theoretically the CIA can’t pull this shit with. Now, if a requestor asks for “any and all records that mention or refer to Subject X” (as opposed to “any and all records that related to Subject X”), the CIA can’t automatically reject the request as overbroad. But of course you’re likely going to have to sue to force the CIA to comply. But when you do, if you cite the case Shapiro v. CIA, you’ll have a strong argument on this point. The CIA will still come up with other reasons not to comply with your request, which may or may not prove successful, but at least you’ll have a good case on this point.
5-Documents POTP sued for and got access to regarding Nelson Mandela
This post is Part Five of our Full Coverage of the January 11 Raw Thought Salon with Ryan Shapiro. Full Index here.
(As explained by Ryan Shapiro at the January 11, 2019 Raw Thought Salon.)
Ryan: At Property of the People, we target intelligence agency documents on a wide range of issues pertaining to the policing of dissenting in the name of national security. One area of concentration for us is records showing the role of U.S. intelligence agencies in the surveillance and suppression of the movement against South African Apartheid. As part of this project, we exposed the FBI targeting of Nelson Mandela and the anti-Apartheid movement as a Communist plot imperiling U.S. national security.
This included, but was not limited to, the FBI placement of a confidential informant within Nelson Mandela’s inner circle, in order to provide political information to the FBI on Mandela and his anti-apartheid associates, while the FBI was tasked with protecting Mandela upon Mandela’s post-prison tour of the United States in 1990. (See Property of the People’s The Mandela Files documents.)
6-Documents POTP sued for and got access to regarding President Trump and his violation of the Constitution’s Emolument Clause
This post is Part Six of our Full Coverage of the January 11 Raw Thought Salon with Ryan Shapiro. Full Index here.
(As explained by Ryan Shapiro at the January 11, 2019 Raw Thought Salon.)
Ryan: Once Trump was elected, we expanded our focus to cover not just intelligence agencies, but the entire Trump Administration. As part of this work, we’ve now exposed numerous sets of violations by the president of the Domestic Emoluments Clause of the Constitution, which is the Constitution’s domestic Anti-Bribery clause. (See Property of the People’s “Profiting off the Presidency” and related “Operation 45” project).
| Tickets to March 8 Raw Thought | Raw Thought Catch Up Fund |